InfoSec Write-ups – Medium–
Protect your business from a DoS attack, with your firewall

Of all the cyber threats in the past 30 years, a denial of service attack is probably the most known and complex for your business . that being said, it is the simplest to perform, here is an article about doing one against my home router https://medium.com/bugbountywriteup/some-may-call-it-a-dos-attack-i-just-tried-to-find-how-my-streamer-behaves-under-stress-36fead7643e4?source=friends_link&sk=2dcdae27987fdf4ea862e61c47d7b3d6
There are many types of DoS attacks, but the idea is the same, attackers want to overwhelm your critical infrastructure and leave it unavailable for your customers and employees.
The bad stuff
- Most DoS attacks utilize well-known ports like port 80
- DoS attacks are distributed
- They can be performed using low CPU appliances as IP cameras
- Firewalls alone are not enough
- Attacks are becoming complex, using layer 3,4 and 7
- IPS inspection will take up resources that may be needed for other operations
- Detection by IPS engines can lead to false-positive events
- New DoS techniques emerge
DOS attacks can be very fast as in ICMP flood Attack, and very slow, as in the slowloris attack https://en.wikipedia.org/wiki/Slowloris_(computer_security)
The enemy within
A DOS attack can start from internal sources for no reason at all, or can be controlled from botnets connecting to an infected PC.
DDOS attacks can be mitigated quickly using network behavior analysis ( once you have a stable baseline of your network ) with rate based threshold that can alert and protect from anomalies such as too many SYN requests sent in one second from one source or towards one destination, CPU overload …
Having said so, in this article we will look at a simple attack using ICMP flood and how to protect it using our IPS and A DDOS policy. so let’s start
Step 1
I assume that you have your LAN and WAN all set up, Our task is to protect your WAN interface from malicious ICMP flood Attacks, where an attacker tries to overwhelm your servers with ICMP echo requests. The ICMP echo requests are known also as PING used in troubleshooting connectivity issues
On your FortiGate navigate to policies & objects

Choose IPV4 DoS Policy
Your DOS policies ( there are many types of policies in your FortiGate firewall, one of them is the DOS policies ) uses the FortiGate IPS engine, to track different anomalies that happen in your network.
An IPS ( intrusion prevention system ) engine is a part of every Next-generation firewall as in FortiGate, checkpoint, Paloalto firewalls. Its main task is to protect your network from 2 things: anomalies, unusual behavior in the network ( as a sudden rise in UDP packets ), or higher CPU percentage and exploits using well-known signatures
Your FortiGate IPS uses signature databases, but it also does one more thing, it decodes well-known protocols, and looks at their internals, doing that, it checks, are the packets of the traffic in place, does it behave according to the standard, a good example can be an ICMP packet that is sent towards your WAN interface. The standard for such a packet is in most cases 56 bytes ( not including headers ), another cause can be too many HTTP headers that is not according to the standard


Step 3 — choose new Dos Policy
When you choose to create a new DoS policy, you will be treated with the following screen
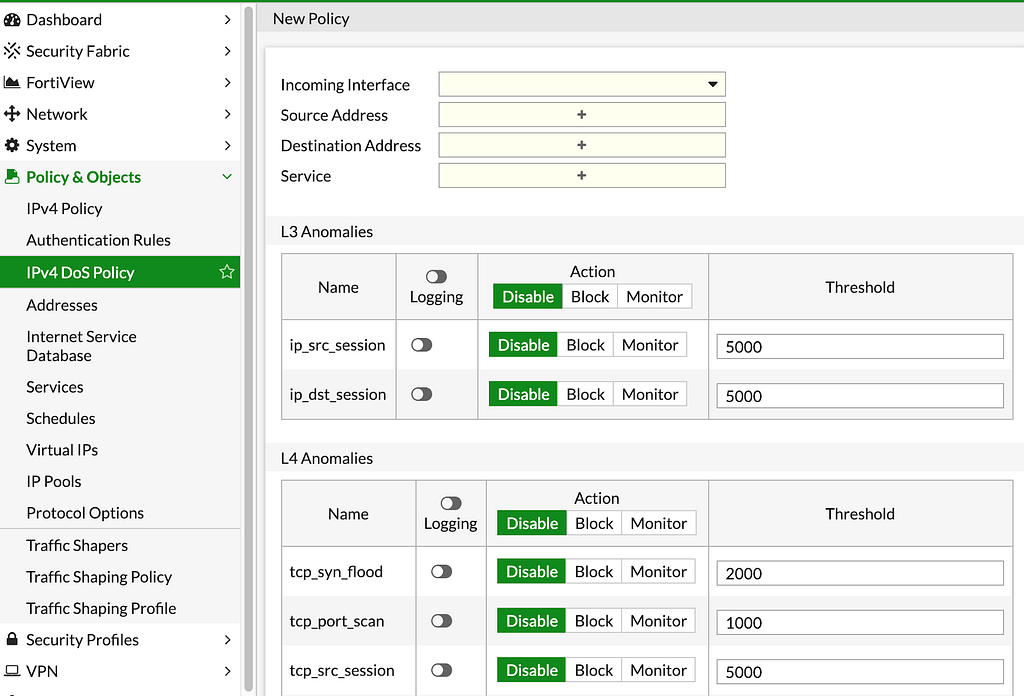

Here you will configure different layer 3 and layer 4 anomalies
The first information that you need to supply is the incoming interface which is usually your WAN interface, as for the source address, destination, and service, you can be very granular, but for most cases, we will use ALL

And now comes the part where you actually create the different sensors, that will track anomalies. you can apply your sensors to 4 protocols:
- TCP
- UDP
- ICMP
- SCTP
You can also apply different sensors for different layers in one policy
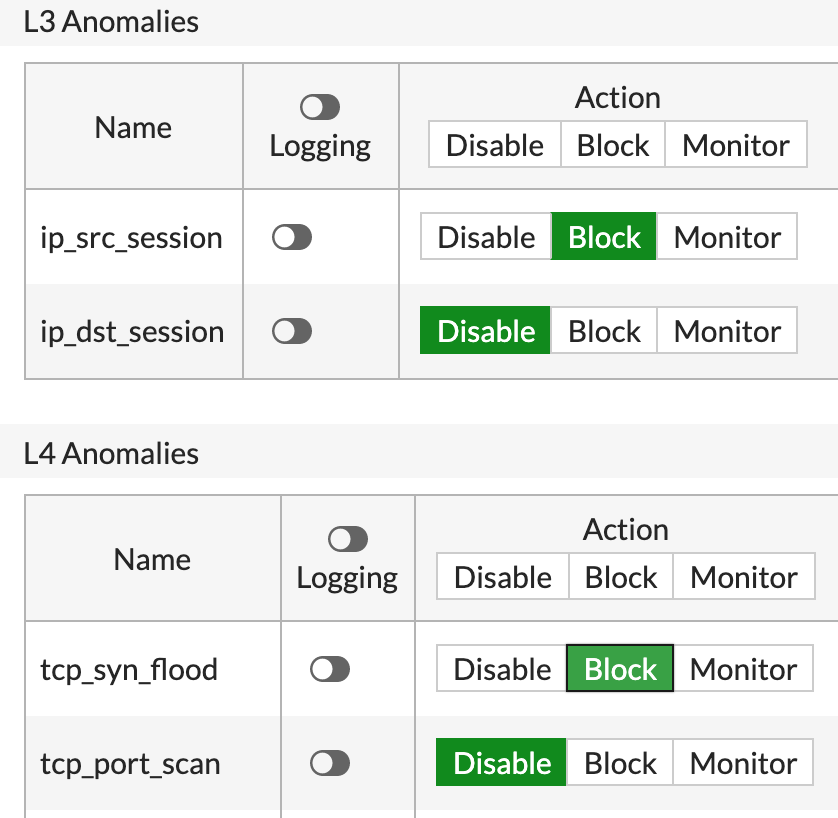
The main anomalies that you will see in the Policy are:
- Flood- detects large volume of the protocol
- Sweep/scan- detects probing attempts
- Source- detects a large volume coming from a single IP
- Destination- detects a large volume heading to a single IP
On the right side of each sensor, you will notice, thresholds, each anomaly has its threshold, that you can ( and advised ) to do so based on your topology and network baseline
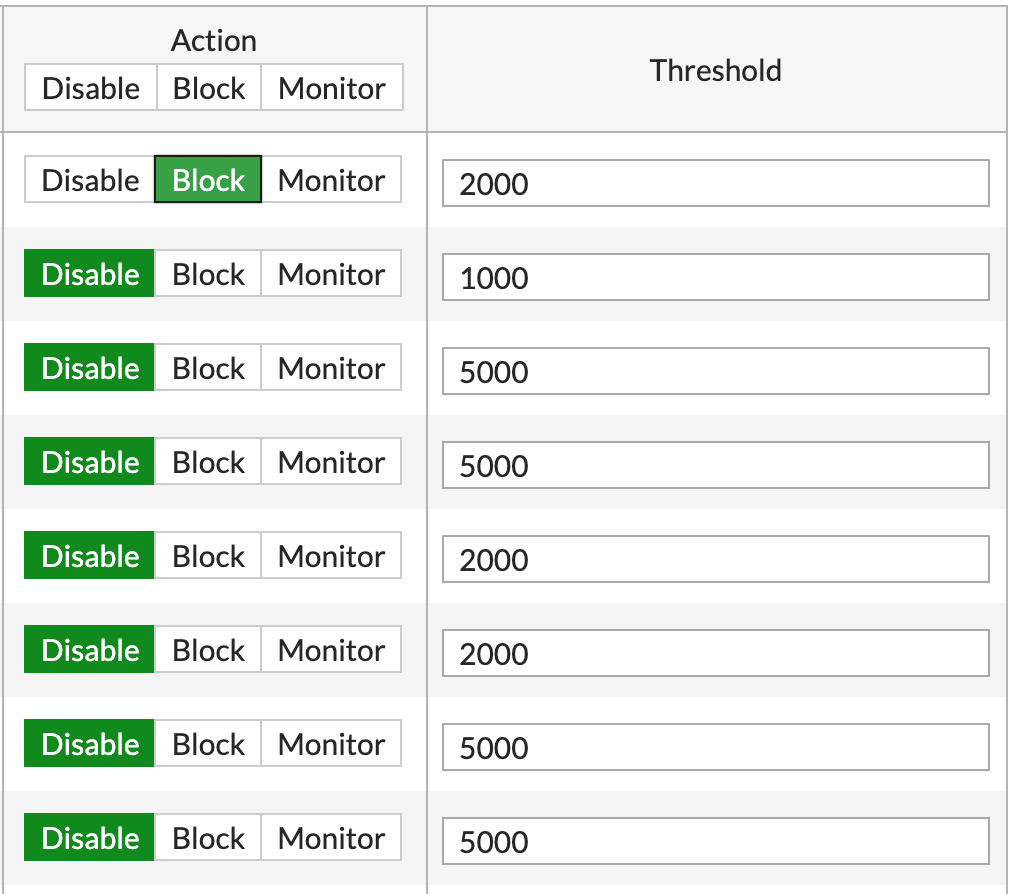
The threshold for the sweep, flood, and scan sensors are defined as the number of sessions a second
So, how do we configure an ICMP flood DOS sensor
Navigate to the layer 4 anomalies
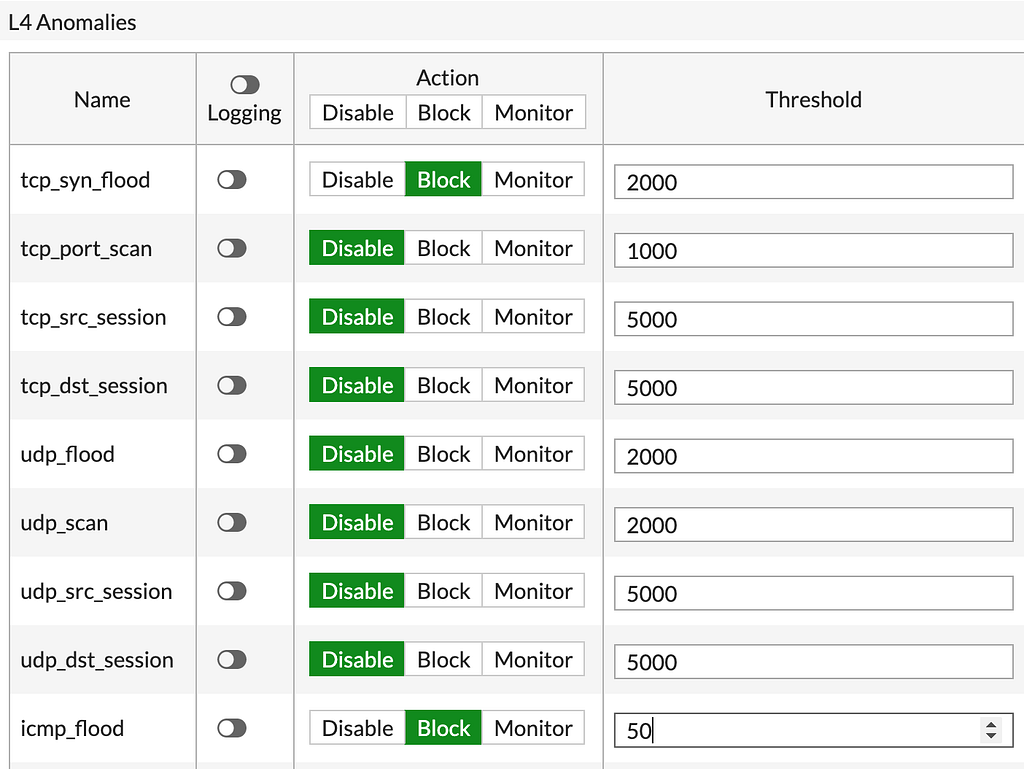
In the Action Pane, choose Block
In the threshold pane, choose the number of ICMP’s in seconds. if you choose 50 for example, your sensor will drop packet number 51
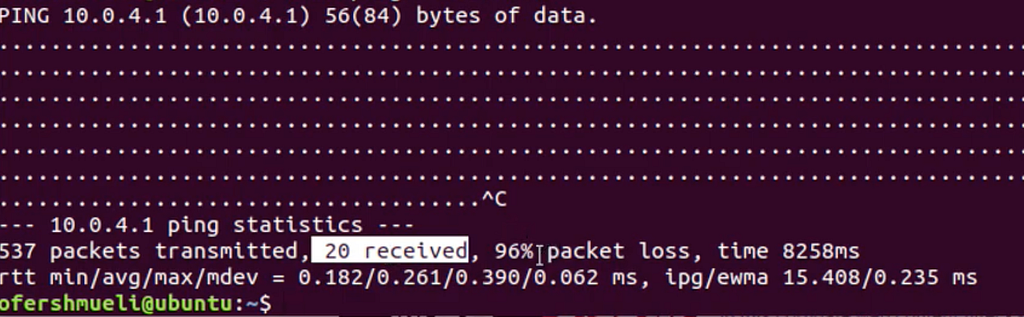
A screenshot that is taken from my Linux machine where I initiated a flood attack against my home gateway, yet it was stooped after 20 packets, following my IPS anomaly threshold
You can subscribe to my channel at youtube.com/fortitip or join my FortiGate courses at https://www.udemy.com/course/fortigate-admin-crash-course/?referralCode=0B534DCF7A6D8BD3417E
Protect your business from a DoS attack with your firewall was originally published in InfoSec Write-ups on Medium, where people are continuing the conversation by highlighting and responding to this story.
